Introducing the Gorgon Cyber Defense System.
Using military principles to defend your home / office, small business, or work from home enterprise workforce.
Increase your defense against hackers that want to steal your identity, security codes, banking details, intellectual property, or private information; or hold you to ransom, or simply destroy your digital property.




The Gorgon Cyber Defense System uses military tactics to deploy many sentry decoys (fake computers) on your network and provides a rapid response option to counter-attack any malicious intruder. No Cyber experience required - just touch a button or allow it to operate autonomously. Get expert help along the way in plain English.
Decoys have famously been used by militaries around the world since the beginning of conflicts and have been proven to be effective to this day.
The Gorgon Cyber Defense System is the only product on the market that deploys an entire swarm of decoys out of the box. Out patent pending technology requires no specialist cyber know-how.
Don't allow someone to steal your identity, banking details, intellectual property or hold you to ransom with impunity. With the Gorgon Cyber Defense System you are no longer helpless or a sitting duck.


As Sun Tzu says “All warfare is based on deception. Hence, when we are able to attack, we must seem unable; when using our forces, we must appear inactive; when we are near, we must make the enemy believe we are far away; when far away, we must make him believe we are near.”
Sun Tzu understood that to gain an advantage over your opponent you need to catch then off guard, make then believe you’re something you are not.
A decoy must be believable, hence Gorgon Cyber mimics your real computers.
As consumers and businesses we should all supplement our security with this ageless and tested decoy technique against cyber attackers.
The Gorgon Cyber Defense System is a small tablet style device that plugs into your network and helps monitor it for malicious intrusions by using decoys. It does not replace your firewall, your anti-virus or malware scanners, rather it augments them and adds a unique new layer of defense.


When someone intrudes on your network, their first priority is usually to attempt to infect and control as many computers as possible. Computers can be anything from servers, to laptops, phones, backup devices, printers, and any smart devices eg TVs, watches, security systems, speakers, cameras, fridges, etc.
The Gorgon Cyber Defense System initially takes 24 hours to learn what is on your network, then starts up to 25 fake devices that deceptively mimics existing computers. It also continues to learn if and when your network devices change. So if you have a single smartphone, a hacker (human or machine) will suddenly see many smartphones, with the same make, model, operating system and so on. The hacker trying to infect, damage or steal things will not know of the decoys and any attempt to connect to one of the decoys instantly triggers an alert, and the defense system is now in action.
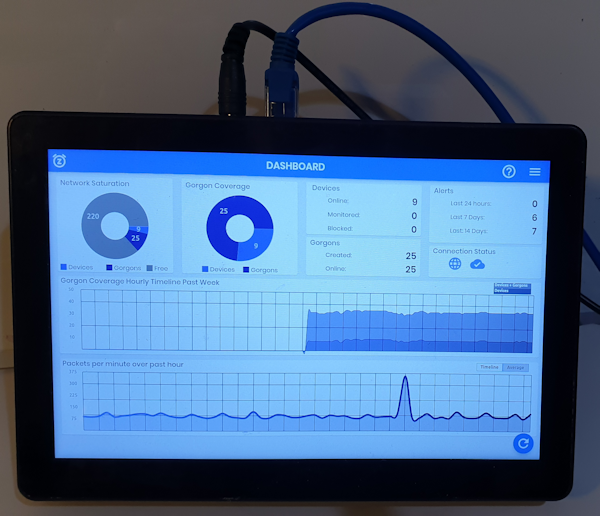
The Gorgon Cyber Defense System comes with a dictionary of common network interactions. When you receive an alert, you can get instructions in plain English, suggesting what to do next.
If it is highly likely to be an attack, the Gorgon Cyber Defense System has the ability to launch a non-destructive counter-attack immediately against the suspicious real device and will attempt to knock it completely off the network and the internet.
You can even start such a counter-attack automatically or remotely via our secure portal. The counter-attack buys you time until the compromised device can be physically disconnected and inspected. This could make all the difference.

The Gorgon Cyber Defense System has been over a year in the making. We are proud to offer comprehensive features for both the basic home office user and also Cyber professionals.
Need more details? Click on the Features Tab
20% of small businesses have experienced a cyber-attack in the last 12 months, resulting in the loss of critical data, identity and credentials theft, intellectual property theft, ransom demands and reputation loss.
Cyber defense has to date been very costly and too complex for most small business and home offices. Our mission is to change that in a way that also does not break the bank.!